
Speak with a Security Expert
Other content in this Stream
Today’s security leaders have limited resources while facing a nearly infinite number of systems, services, solutions, and threats.
Spiraling inflation and the pervading security skills gap have security leaders struggling to keep up. Our new eBook outlines strategies gathered from 50+ leaders.
Recently updated for 2023 and packed with incredible insights, the latest version of The Security Leader's Handbook is a must-have resource for cybersecurity leaders like you.
HackerOne Security Advisory Service is designed to optimize the outcomes of your continuous security strategies and ensure your security safety net is strong.
Learn how Zebra Technologies leveraged the HackerOne Platform to improve customer trust, gain more robust coverage for rogue digital assets, increase oversight and confidence in security, and achieve
![Common Vulnerability Scoring System [CVSS] | A Complete Explanation](jpg/tilebg-blogs659b.jpg?url=https%3A%2F%2Fwww.hackerone.com%2Fsites%2Fdefault%2Ffiles%2FHAC_Blog_Common%2520vulnerability%2520scoring%2520system-Main_Featured_560x494_L2R1.png&size=1&version=1690208403&sig=1fd82a9e68b87934c3b28aa3aa5ddfcb&default=hubs%2Ftilebg-blogs.jpg)
How Does CVSS Work? Vulnerabilities are flaws in an organization's internal controls, information systems, or processes that cybercriminals can exploit to steal corporate data and cause...

In the last two years of their bug bounty program, the hacker community has helped TikTok identify and disclose 450 vulnerabilities in their public-facing assets. In response, TikTok has awarded...
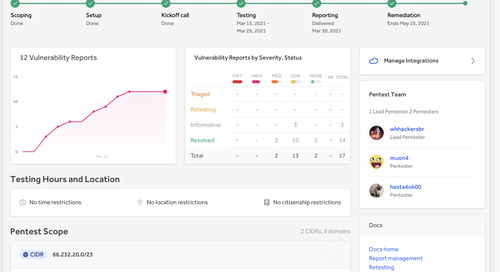
New capabilities improve pentesting to increase attack resistance The enhanced features drive robust security testing practices with the ability to launch, test, identify, retest, and fix...

Today's Hacker rez0 JXoaT: What was your first experience with hacking growing up? rez0: I think, at least for the word 'Hacking,' my experience comes from majoring in computer science. Like, I...
HackerOne Appoints Dawn Mitchell as Chief People Officer ejames@hackerone.com Thu, 08/18/2022 - 09:55 Read more about HackerOne Appoints Dawn Mitchell as Chief People Officer ...
HackerOne Appoints Ilona Cohen as Chief Legal and Policy Officer alice@hackerone.com Wed, 07/13/2022 - 03:38 Read more about HackerOne Appoints Ilona Cohen as Chief Legal and Policy...

Understanding where the critical flaws lie within your organization’s attack surface is critical—but complicated.









